LabVIEW基于Netstat列出活动的网络连接 点击:250 | 回复:0
LabVIEW基于Netstat列出活动的网络连接
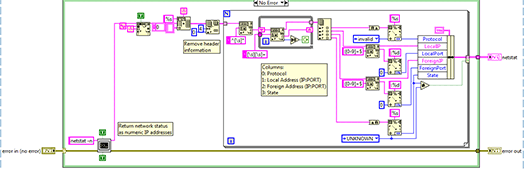
该VI使用命令行“netstat”查询网络堆栈中的活动网络连接。除了连接状态之外,还会返回活动的本地和外部 IP 地址和端口号。
连接状态:Netstat 返回每个网络连接的状态,如下表所示。
State | Description |
LISTEN | accepting connections |
ESTABLISHED | connection up and passing data |
SYN_SENT | TCP session has been requested by us; waiting for reply from remote endpoint |
SYN_RECV | TCP session has been requested by a remote endpoint for a socket on which we were listening |
LAST_ACK | TCP our socket is closed; remote endpoint has also shut down; we are waiting for a final acknowledgement |
CLOSE_WAIT | TCP remote endpoint has shut down; the kernel is waiting for the application to close the socket |
TIME_WAIT | TCP socket is waiting after closing for any packets left on the network |
CLOSED | socket is not being used |
CLOSING | TCP our socket is shut down; remote endpoint is shut down; not all data has been sent |
FIN_WAIT1 | TCP our socket has closed; we are in the process of tearing down the connection |
FIN_WAIT2 | TCP the connection has been closed; our socket is waiting for the remote endpoint to shut down |
程序截图如下所示。
更多的介绍,参见如下介绍,原文: http://linux-ip.net/html/tools-netstat.html
G.4. netstat
The netstat utility summarizes avariety of characteristics of the networking stack. With netstat you can learn a numberof important things. If no other type of data is requested it will report onthe state of all active sockets. You can however request the routingtable, masquerading table, network interface statistics, and networkstack statistics [60].
G.4.1. Displaying socket status with netstat
One of the most common uses ofthe netstat utilityis to determine the state of sockets on a machine. There are many questionsthat netstat cananswer with the right set of options. Here's a list of some of the thingsdifferent things we can learn.
· whichservices are listening on which sockets
· whatprocess (and controlling PID) is listening on a given socket
· whetherdata is waiting to be read on a socket
· whatconnections are currently established to which sockets
Byinvoking netstat withoutany options, you are asking for a list of all currently open connections to andfrom the networking stack on the local machine. This means IP networkconnections, unix domain sockets, IPX sockets and Appletalk sockets amongothers. Naturally, we'll skip over the non-IP sockets since this is about IPnetworking with linux.
Assumethe --inet switchin all cases below unless we are examining a particular higher layer protocol(e.g., TCP with the --tcp switch or UDP with --udp switch.
Aconvenient feature of netstat isits ability to differentiate between two different sorts of name lookup.Normally the -n specifies no name lookup, butthis is ambiguous when there are hostnames, port names, and user names.Fortunately, netstat offersthe following options to differentiate the different forms of lookup andsuppress only the [un-]desired lookup.
· --numeric-hosts
· --numeric-ports
· --numeric-users
Theoption -n (my favorite), suppress all hostname, port name andusername lookup, and is a synonym for --numeric. I'll reiterate that hostnames andDNS in particular can be confusing, or worse, misleading when trying todiagnose or debug a networking related issue, so it is wise to suppresshostname lookups in these sorts of situations.
In Example G.11,“Displaying IP socket status with netstat” we will look at netstat's numeric output and thenwe'll invoke the same command but suppress the host lookups. Though the outputis almost the same, a particular situation might call for one or the otherinvocation.
Example G.11. DisplayingIP socket status with netstat
[root@morgan]# netstat --inet -n Active Internet connections (w/o servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 192 192.168.98.82:22 192.168.99.35:40991 ESTABLISHED tcp 0 0 192.168.98.82:42929 192.168.100.17:993 ESTABLISHED tcp 96 0 127.0.0.1:40863 127.0.0.1:6010 ESTABLISHED tcp 0 0 127.0.0.1:6010 127.0.0.1:40863 ESTABLISHED tcp 0 0 127.0.0.1:38502 127.0.0.1:6010 ESTABLISHED tcp 0 0 127.0.0.1:6010 127.0.0.1:38502 ESTABLISHED tcp 0 0 192.168.98.82:53733 209.10.26.51:80 SYN_SENT tcp 0 0 192.168.98.82:44468 192.168.100.17:993 ESTABLISHED tcp 0 0 192.168.98.82:44320 192.168.100.17:139 TIME_WAIT [root@morgan]# netstat --inet --numeric-hosts Active Internet connections (w/o servers) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 192.168.98.82:ssh 192.168.99.35:40991 ESTABLISHED tcp 0 0 192.168.98.82:42929 192.168.100.17:imaps ESTABLISHED tcp 0 0 127.0.0.1:40863 127.0.0.:x11-ssh-offset ESTABLISHED tcp 0 0 127.0.0.:x11-ssh-offset 127.0.0.1:40863 ESTABLISHED tcp 0 0 127.0.0.1:38502 127.0.0.:x11-ssh-offset ESTABLISHED tcp 0 0 127.0.0.:x11-ssh-offset 127.0.0.1:38502 ESTABLISHED tcp 0 0 192.168.98.82:53733 209.10.26.51:http SYN_SENT tcp 0 0 192.168.98.82:44468 192.168.100.17:imaps ESTABLISHED tcp 0 0 192.168.98.82:44320 192.168.100:netbios-ssn TIME_WAIT |
Eachline represents a either the sending or receiving half of a connection. In theabove output on morgan it appears that there are noconnections other than TCP connections. If you are very familiar with TCP portsand the service associated with that port, then the first format will sufficein most cases. A possibly misleading aspect of the latter output is visible inthe connections to and from localhost and the final line. netstat abbreviates the IPendpoint in order to reproduce the entire string retrieved from the port lookup(in /etc/services).Also interestingly, this line conveys to us (in the first output) that thekernel is waiting for the remote endpoint to acknowledge the 192 bytes whichare still in the Send-Q buffer.
Thefirst line describes a TCP connection to the IP locally hosted on morgan'sEthernet interface. The connection was initiated from an ephemeral port (40991)on tristan toa service running on port 22. The service normally running on this well-knownport is sshd, so we can conclude that somebody on tristan hasconnected to the morgan's ssh server. The second linedescribes a TCP session open to port 993 on isolde, which probably means that the useron morgan hasan open connection to an IMAP over SSL server.
Thethird through the sixth lines can be understood in pairs. By examining thesource and destination IP and port pairs, we can see that two different TCPsessions have been established with the source and destination address of127.0.0.1. For an administrator to publish services on localhost is not at alluncommon. This makes the service harder to abuse from the network. In thiscase, when we allow the service lookup, the port in question (6010) appears tobe used to tunnel forwarded X applications over ssh.
Thenext line is the first TCP session in our output which is not in a state ofESTABLISHED. Refer to Table G.1, “Possible Session States in netstat output” for a full list ofthe possible values of the State field in the netstat output. The stateSYN_SENT means that an application has made arequest for a TCP session, but hasnot yet received the return SYN+ACK packet.
Thefinal line of our netstatoutputshows a connection in the TIME_WAIT state, which means that the TCP sessions havebeen terminated, but the kernel is waiting for any packets which may still beleft on the network for this session. It is not at all abnormal for sockets tobe in a TIME_WAIT state for a short period of time after a TCP session hasended.
Ifwe needed to know exactly which application owned a particular networkconnection, we would use the -p |--program switchwhich gives us the PID and process name of the owner process. If we want to seethe unix user and the PID and process we'll add the -e | --extend switch.
Example G.12. DisplayingIP socket status details with netstat
[root@masq-gw]# netstat -p -e --inet --numeric-hosts Proto Recv-Q Send-Q Local Address Foreign Address State User Inode PID/Program name tcp 0 0 192.168.100.254:ssh 192.168.100.17:49796 ESTABLISHED root 25453 6326/sshd tcp 0 240 192.168.99.254:ssh 192.168.99.35:42948 ESTABLISHED root 171748 31535/sshd |
Theredoesn't appear to be a large number of connections to and from the masq-gw host.The two sessions are initiated to the sshd running on port 22, and the processwhich owns each socket is a root process.
Table G.1. PossibleSession States in netstat output
State | Description |
LISTEN | accepting connections |
ESTABLISHED | connection up and passing data |
SYN_SENT | TCP; session has been requested by us; waiting for reply from remote endpoint |
SYN_RECV | TCP; session has been requested by a remote endpoint for a socket on which we were listening |
LAST_ACK | TCP; our socket is closed; remote endpoint has also shut down; we are waiting for a final acknowledgement |
CLOSE_WAIT | TCP; remote endpoint has shut down; the kernel is waiting for the application to close the socket |
TIME_WAIT | TCP; socket is waiting after closing for any packets left on the network |
CLOSED | socket is not being used (FIXME. What does mean?) |
CLOSING | TCP; our socket is shut down; remote endpoint is shut down; not all data has been sent |
FIN_WAIT1 | TCP; our socket has closed; we are in the process of tearing down the connection |
FIN_WAIT2 | TCP; the connection has been closed; our socket is waiting for the remote endpoint to shut down |
G.4.2. Displaying the main routing table with netstat
One of the most common uses of netstat, especially incross-platform environments is the reporting of the main routing table. On manyplatforms, netstat -rn isthe preferred method of displaying routing information, although linux providesat least two alternatives to this: route and ip route show.
Example G.13. Displayingthe main routing table with netstat
[root@morgan]# netstat -rn Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface 192.168.98.0 0.0.0.0 255.255.255.0 U 40 0 0 eth0 127.0.0.0 0.0.0.0 255.0.0.0 U 40 0 0 lo 0.0.0.0 192.168.98.254 0.0.0.0 UG 40 0 0 eth0 |
Thisoutput should look familiar. The routing cache itself may not be as familiar tomost, but can also be displayed with netstat. The ouput below is exactly the same as theouput from route -enC.Refer also to Example D.3, “Viewing the routing cache with route”.
Example G.14. Displayingthe routing cache with netstat
[root@tristan]# netstat -rnC Kernel IP routing cache Source Destination Gateway Flags MSS Window irtt Iface 194.52.197.133 192.168.99.35 192.168.99.35 l 40 0 0 lo 192.168.99.35 194.52.197.133 192.168.99.254 1500 0 29 eth0 192.168.99.35 192.168.99.254 192.168.99.254 1500 0 0 eth0 192.168.99.254 192.168.99.35 192.168.99.35 il 40 0 0 lo 192.168.99.35 192.168.99.35 192.168.99.35 l 16436 0 0 lo 192.168.99.35 194.52.197.133 192.168.99.254 1500 0 0 eth0 192.168.99.35 192.168.99.254 192.168.99.254 1500 0 0 eth0 |
Consult Section D.1.1,“Displaying the routing table with route” formore detail on reading and interpreting the data in this output. Because thisis simply another way of reporting the routing table information, we'll skipover any detailed description.
G.4.3. Displaying network interface statisticswith netstat command
netstat -i summarizes interface statistics in a terse format. Thisformat
OK!This is strange. netstat -ie looksexactly like ifconfig output.That's weird!
G.4.4. Displaying network stack statistics with netstat
G.4.5. Displayingthe masquerading table with netstat
For machines which performmasquerading, typically dual-homed packet-filtering firewalls like masq-gw atool to list the current state of the masquerading table is convenient.
Eachmasqueraded connection can be described by a tuple of six pieces of data: thesource IP and source port, the destination IP and destination port, and the(usually implicit) locally hosted IP and a local port.
Example G.15. Displayingthe masquerading table with netstat
[root@masq-gw]# netstat -Mn |
FIXME;this command seems to fail on all of the iptables boxen, even if I'm usingthe -j MASQUERADE target. I can use it successfully on ipchainsboxen. Anybody have any ideas or explanation here?
[60] Additionally, netstat can display multicastinformation with the --group switch. I have zero experience here.Anybody with experience want to write about this?
需要说明的是,上述的例程和文档,都是可以下载的,双击即可打开,其中压缩文件是可以采用粘贴复制的方式,拷贝到硬盘上。这不是图片,各位小伙伴看到后尝试一下,这个问题就不用加微信咨询了。有关LabVIEW编程、LabVIEW开发等相关项目,可联系们。附件中的资料这里无法上传,可去公司网站搜索下载。
楼主最近还看过
- EPLANP8部件库导入时意外丢失...
 [5318]
[5318] - 困惑:没人提到却非常重要的问...
 [2346]
[2346] - OPC简介
 [5098]
[5098] - MCGS6.2通用版授权无限点
 [27524]
[27524] - 哪位知道OSI软件公司(生产PI...
 [3882]
[3882] - Webaccess如何不使用脚本将整...
 [2216]
[2216] - opc-deadband(死区)如何使用...
 [6672]
[6672] - 施耐德M340默认IP地址计算方...
 [9768]
[9768] - 求助:AB PLC仿真软件
 [6125]
[6125] - VB界面上的控件与串行口的连...
 [2220]
[2220]

官方公众号

智造工程师
-

 客服
客服

-

 小程序
小程序

-

 公众号
公众号

















 工控网智造工程师好文精选
工控网智造工程师好文精选
